NFV Evolution: Defining the Missing Link
- Reduced operator CAPEX and OPEX through reduced equipment costs and reduced power consumption
- Reduced time-to-market to deploy new network services
- Improved return on investment from new services
- Greater flexibility to scale up, scale down or evolve services
- Openness to the virtual appliance market and pure software entrants
- Opportunities to trial and deploy new innovative services at lower risk
Of these benefits, accelerating new service delivery is top of mind as the primary driver among network operators. The pressure placed on CSPs from over the top (OTT) providers like Google Voice, Skype, and WhatsApp are substantial. Never in the history of telecom have the business’ core services been so threatened. CSPs simply can’t afford to wait 12 months, a typical development cycle today, to release competing offerings.
An Infonetics Research survey in July, 2013, found that operators are in select domains, but eager to move faster. “For the most part, carriers are starting small with their SDN and NFV deployments, focusing on only parts of their network, what we call ‘contained domains,’ to ensure they can get the technology to work as intended,” wrote Michael Howard, co-founder and principal analyst for carrier networks at Infonetics Research. He added, “But momentum for more widespread use of SDN and NFV is strong, as evidenced by the vast majority of operators participating in our study who plan to deploy the technologies in key parts of their networks, from the core to aggregation to customer access. Even so, we believe it’ll be many years before we see bigger parts or a whole network controlled by SDNs.”
NFV in the Evolved Packet Core (EPC)
The benefits of NFV as it applies to mobile packet core networks will most likely be realized in the control plane, especially within EPC deployments. Components such as Mobile Management Entity (MME), Policy and Charging Rules Function (PCRF) and Home Subscriber Server (HSS) rely more on compute resources than packet processing resources. This allows a natural progression to virtualized instances of these functions using NFV.
Typically, MME's are deployed in a clustered and load-balanced configuration to handle call setups, handovers, and radio updates. Traditional MME's are based on large, expensive, and usually custom hardware. Deploying MME's require extensive planning and engineering. As you can see in figure 2 below, with a fully virtualized MME, a mobile operator leveraging NFV can dynamically deploy virtualized MME's during times when loads are high and can decommission MME instances when loads are low. The same concepts can be applied to PCRF and HSS solutions.
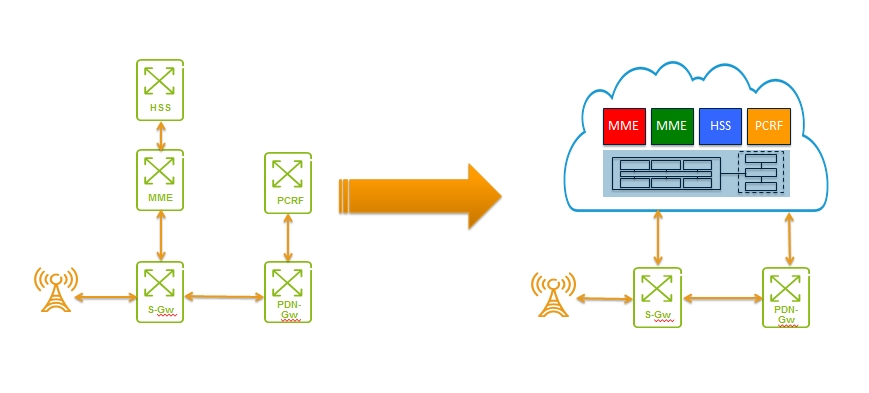
Figure 2 - Virtualizing Mobile Managment Entities (MMEs)
Source: Tail-f Systems
NFV Challenges
While ETSI’s framework offers a nice overview of NFV, there are many pieces left out of the equation, as well as challenges related to upending the status quo. To leverage the potential benefits, there are a number of technical deficits which need to be addressed. A white paper published in October, 2012, by a group of 13 global services providers outlined the following challenges:
- Virtualized network appliances must be portable between different hardware vendors, and with different hypervisors.
- Virtualized network elements must coexist with legacy hardware while enabling an efficient migration path to fully virtualized network platforms.
- Network Functions Virtualization will only scale if all of the functions can be automated.
- Network operators need to be able to mix and match hardware from different vendors, hypervisors from different vendors and virtual appliances from different vendors without incurring significant integration costs and avoiding lock-in.
- Operators must be able to manage and orchestrate many virtual network appliances while ensuring security from attack and misconfiguration.


















