Restoring Telecom Trust
2. STIR/SHAKEN for Caller ID Authentication and Verification
STIR/SHAKEN is used to perform caller ID authentication at origination and verification at call termination.
These James-Bond-inspired acronyms stand for Secure Telephony Identity Revisited (STIR), developed by the Internet Engineering Task Force (IETF), and Secure Handling of Asserted information using Tokens (SHAKEN), developed by ATIS and the SIP Forum.
But don’t worry about these arcane names. The important thing to know is that STIR/SHAKEN is used to prevent caller ID spoofing. Here’s how.
As a service provider is originating an outbound call for its customer, it will use the technology in conjunction with its subscriber information to attest to its confidence about two things:
1. That it knows the customer making the call.2. That this customer’s use of the calling number is legitimate.
The attestation and related call information is then put into a digitally signed Identity token that is sent with the call. This is now a signed call.
When a terminating service provider receives a signed call, it uses the technology to verify that:
- The signature is correct.
- The Identity token information matches the asserted caller ID.
- This information hasn’t been changed since the call was signed.
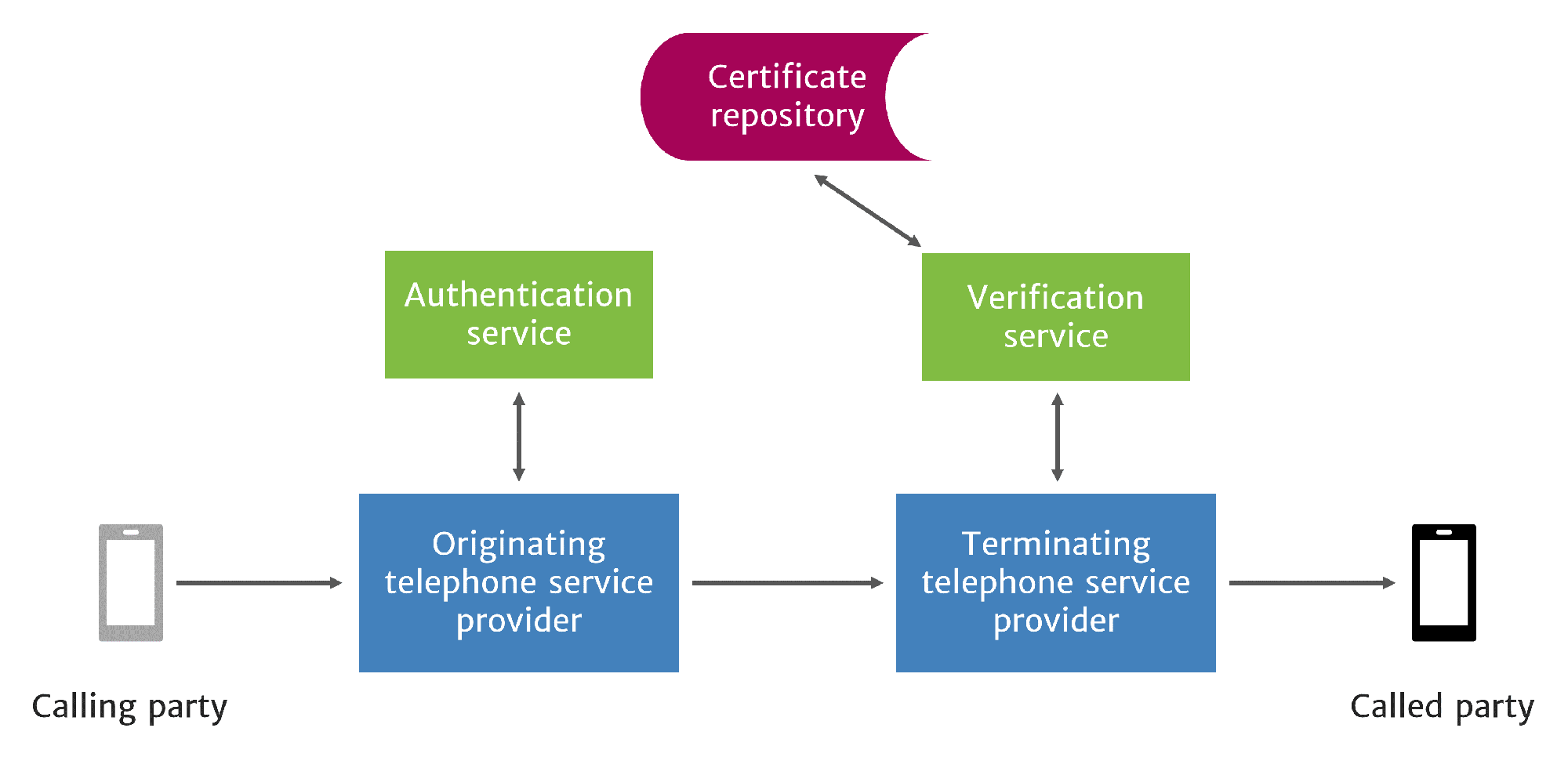
Figure 2: STIR/SHAKEN Network Flow
The service provider then puts verification status into the call data, which the handset displays to the called party (see figure 2).
To prevent clever robocall perpetrators from spoofing authentication, the technology uses Public Key Infrastructure. The originating provider digitally signs outbound calls with its private key, and the terminating provider verifies these signatures with the originating providers’ public key. These keys are associated with digital certificates, which are assigned to legitimate service providers by a trusted governance authority. Robocall perpetrators can’t get in on it.
STIR/SHAKEN throws new obstacles in the path of robocall perpetrators:
- If a robocall perpetrator spoofs caller ID, then their robocalls will not be authenticated and digitally signed. Terminating service providers will not indicate to their subscriber that the incoming call was verified.
- If a robocall perpetrator replayed or spoofed an Identity token, then it would fail verification and the terminating service provider would apply an appropriate policy to the call (e.g., block or divert).
In the early days of STIR/SHAKEN, before widespread adoption of this technology, most calls will be unsigned and will not raise suspicion. As the technology becomes ubiquitous, subscribers will become more likely to answer verified calls and let unsigned calls go to voicemail.



















