Simplifying the Network Edge with SDN
An SDN-based solution to
load balancing for cybersecurity
Both hardware and software elements are needed to achieve the benefits outlined above. These include programmable white-box networking hardware, network operating systems optimized for these platforms, and SDN-based control layer software that together enable the transfer of key network functions directly into the forwarding plane.
The benefits of this approach are not merely academic. They have been amply demonstrated by commercial deployments with NoviFlow customers who have deployed NoviFlow’s CyberMapper Security Load Balancer control software in combination with Intel/Barefoot Tofino-based white-box switches running NoviFlow’s NoviWare NOS.
Figure 1 shows how using this approach was used to greatly simplify architecture at the network/cloud edge.
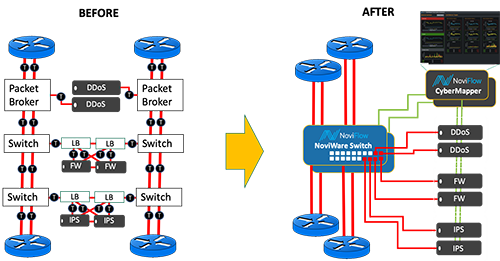
Figure 1 - Simplifying Network/Cloud Edge Architecture
Unlike conventional non-SDN network solutions, this solution has made it possible to leverage the disaggregation of data and control planes to enable these to scale independently, making for greater overall solution modularity. It also makes possible the redistribution and redeployment of network resources in real-time as networking demand fluctuates, even into the Terabit range. Network services usually delivered at the network’s edge (such as security assets, e.g. DDoS, firewalls, etc.) are pooled together and made accessible from anywhere in the entire network, reducing total service costs by sharing capacity over multiple locations rather than overprovisioning each ingress or egress point.
Increased and transparent modularity also make it possible to dynamically scale cybersecurity functions and multi-server tool farms into the Terabit range, and to independently scale the capacity of control and data planes.
The ability to change network functionality via software also enables faster prototyping and rollout of new networking functionality and protocols such as INT and eliminates forced obsolescence of networking equipment as network hardware, which can then be reprogrammed and repurposed according to need.
A key cybersecurity benefit of this approach is that it separates the network operations domain from the network security domain, finally providing network security managers direct access to security services without their actions being filtered and—more importantly—delayed by network operations. AI and ML-based analytics can be employed to detect and mitigate cyber incursions in machine-time, significantly reducing response times and improving protection from DDoS-style attacks as well as attempts to disrupt, damage or steal network assets.
Conclusion
SDN techniques and programmable match-action network processors can be leveraged to optimize cybersecurity applications—and almost any virtualized network function requiring multiple servers—by transferring load balancer, packet broker and telemetry functions directly within the network fabric. This transforms the forwarding plane into an integral and fully programmable element of organizations’ information processing capacity. Furthermore, the effectiveness and cost advantages of this approach have been demonstrated in multiple commercial deployments at tier-1 service providers around the world.



















