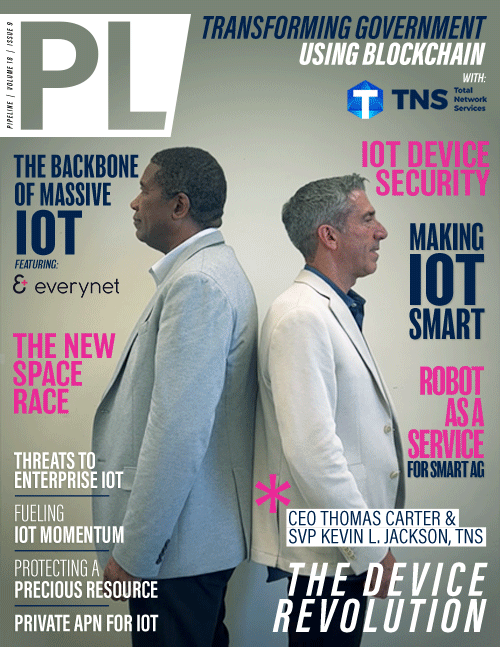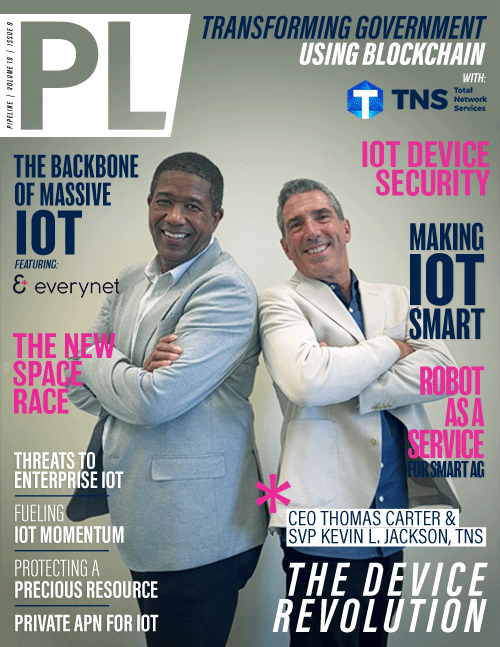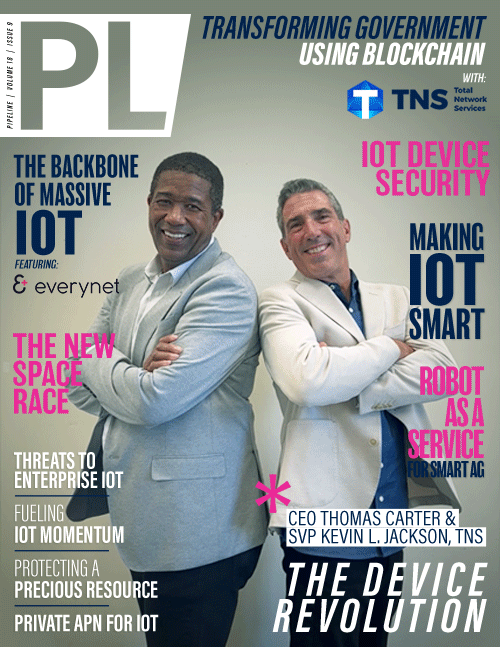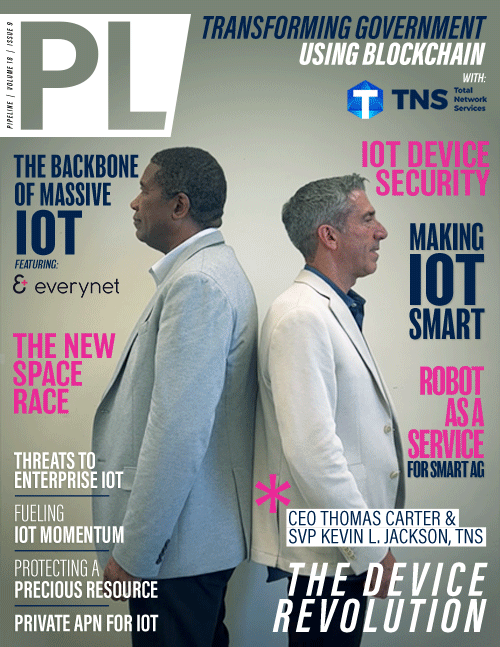
Federal Government Transformation
Using Blockchain
the use of counterfeit devices. They are also creating an immutable trail of custody on data for all medical claims related to field injuries and incidents.
“Via device orchestration and security, we can make sure that information on Census workers is not inadvertently shared, triggering HIPAA violations and more,” Eric said. Beyond EMMA and the census, the potential for this technology is enormous, with a total addressable market of billions of connected devices that Transforma has predicted will grow to $1.5 trillion in value by 2030.
As the IoT momentum accelerates and the world becomes more dependent upon connected devices, end users may simply assume that their devices, data, and the underlying networks are secure. But this may be a gross miscalculation.
In 2008, Kevin Fu from the University of Massachusetts, Amherst demonstrated the real cybersecurity risks for surgically implanted connected medical devices including cardiac pacemakers and defibrillators. Fu was able to hack these implanted medical devices to drain the battery that was meant to last years to just weeks; and use them to shock a heart with 700 volts of electricity. Since then, there has been an increase in the number, sophistication, and variety of attacks on connected medical devices, including insulin pumps. And that’s just the device risk. There’s an entire market built around the selling of medical data and it’s up to 50 times more valuable than credit card information. Quantum-level cybersecurity attacks will be increasingly focused on the advanced persistent threat or sabotage levels, in addition to data theft and ransomware.
Medical identity data can include social security numbers, credit card numbers, and much more. Hacking sensitive medical information enables someone to make an insurance claim on your behalf, or to collect on an insurance policy. But it’s not just about the value of medical data to hackers. A growing market will use medical data and history for diagnoses, tailored care, insurance decisions, and more. The consequences for medical score data can and will be far-reaching.
The recent decision by the US Supreme Court to overturn Roe v. Wade combined with the Affordable Care Act (ACA) amplifies this concern. Setting the headlines aside, Roe set a limitation of the government’s authority to make decisions over one’s own body. The historic decision to overturn Roe now creates the potential to give this authority to the same institution making and paying for medical decisions under the ACA, affecting millions of Americans. The implications for the sharing, use and transmission of medical data are still unknown. But, one can imagine the risks the unintended use or misuse of this information may create.
The rapidly shifting landscape, evolving opportunities, and accelerating adoption of connected devices across industries introduces new complexity for device and data security. This is especially true with the development of large-scale quantum computers that create greater risk in the wrong hands. But Forward Edge-AI has as solution for that.
Under a Cooperative Research and Development Agreement (CRADA), Forward Edge-AI and the National Security Agency (NSA) are commercializing a quantum-resistant encryption device, called Isidore Quantum, to augment IoT and other edge devices. Isidore offers low-cost (under $500), quantum-resistant encryption to protect a wide range of public and private infrastructure systems, including IoT, SCADA, the growing Internet of Medical Things (IoMT), autonomous vehicles, VIP mobile phones, and much more. Given the value of and risk to medical score data, the IoMT use case is a priority, and potential government implementation to protect medical devices is on the horizon.
The combination and application of technologies including AI, blockchain, NTFs, RPA and UCID offers enormous potential—in government and well beyond. “With so many use cases, government is ripe for the adoption of these emerging technologies,” Eric said. “As we demonstrate the successful application of advanced technology for half of a million users and devices within the federal government, the potential to expand is virtually limitless.”
The success of EMMA and the tangible application of emerging technologies unlocks the potential for the IoT, transformation, and innovation across nearly every industry. The massive number of connected devices coming online is staggering, and automation is the key to harnessing efficiency at scale. Many have tried to seize this opportunity ignoring the importance of security and have paid the price. Their names are now synonymous with breach. Think Colonial Pipeline, Dyn, and Solarwinds. TNS, Rypplzz, and Forward Edge-AI have created a unique solution that combines both efficiency and security and it’s getting noticed, attracting millions of dollars in investment to make this unique technology offering a reality.
EMMA serves as an important proof point for the solution as well as the underlying technology, which are key to unlocking efficiency, while mitigating the risks, to capitalize on the IoT opportunity. It’s also essential to ensuring the safety and security of our evolving, global, and increasingly connected society. Innovation may not be occurring where you would expect, but it is happening where it is needed, and it’s needed now.