Hacking 4.0: What will they hack next?
One way to evaluate the vulnerabilities of networks, software and devices is attack simulation, or fuzzing, which emulates aggressive hacking by relentlessly pounding systems and applications, whether in-house or third party, with faulty and unexpected inputs, thus exposing flaws. One solution provider that offers a fuzzing platform is Codenomicon, which partnered with Telcordia in 2011 to help market its unknown-vulnerabilities testing service, Defensics. As you can see in figure 2 below, smart (i.e., internet-connected) television sets expose dozens of exploitable attack surfaces.

Source: “Smart TV Hacking: Crash Testing Your Home Entertainment” (Codenomicon white paper)
Codenomicon performed fuzzing tests on six different smart TVs across six protocols. The results, as illustrated in figure 3, reveal that all vendors have devices that could be compromised by unexpected signaling.
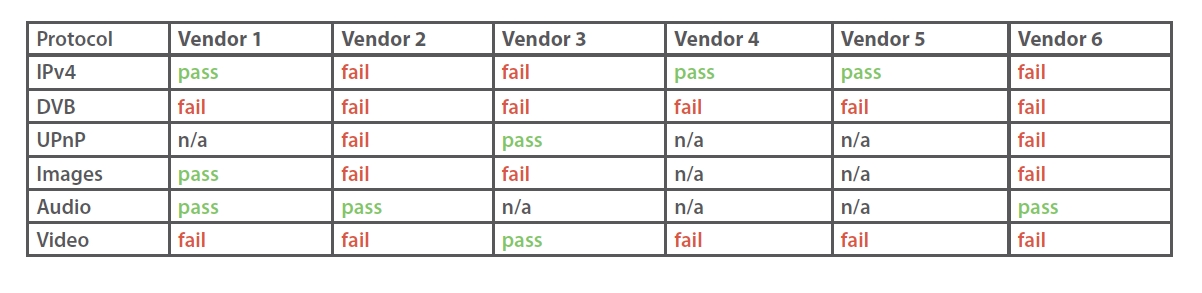
Source: “Smart TV Hacking: Crash Testing Your Home
Entertainment”
By applying fuzzing, network-equipment vendors and network operators can eliminate vulnerabilities and ensure that their resources are bulletproof before they’re “live” on the network. On its website Codenomicon quotes a security-testing expert from Nokia Solutions and Networks (NSN), who commented, “We’ve never had a bug turn up in a product after its release that falls within the region which Codenomicon’s tools test.”
Fuzzing can also be used to expose vulnerabilities in Bluetooth, metro Ethernet, VoIP, LTE, IMS, XML, and hundreds of other protocols, and is one of the best security solutions for next-generation applications. Similar proactive fuzzing tools are available from QualiTest Group and P1 Security.
Another way for CSPs to head off hackers before they strike is threat-information sharing. “Prevention Is Futile in 2020,” a report published in May by the research firm Gartner, states that in seven years “continuous compromise by advanced targeted attacks will require that organizations share security intelligence to better understand where and how they are compromised.”
Historically, security staff from various organizations have shared limited threat information via email or chat messaging, but they lacked a unified, secure platform from which they could collaborate on threat identification and avoidance. But imagine a secure social network that can alert community members to the characteristics and behaviors of malicious software. Security start-up Cyber Squared showcased such a solution, which it calls ThreatConnect, at the Digital Disruption event late last month in San Jose, Calif. Founder and CEO Adam Vincent proclaimed, based on sample analysis, that “companies can save 80 percent” by implementing a threat intelligence-sharing platform.
Addressing security for social networks in an organization starts with threat-awareness training and ends with policy controls. First, since employees often access social networks from the office, it’s important that the same password protocols used in IT be extended to Facebook, Twitter and the like.




















