Hacking 4.0: What will they hack next?
In the mobile sphere the two areas of greatest concern are Android devices and bring-your-own-device (BYOD) deployments. In the United States and Australia, attacks on the former are now more common than those targeting personal computers, as you can see in figure 1 below.
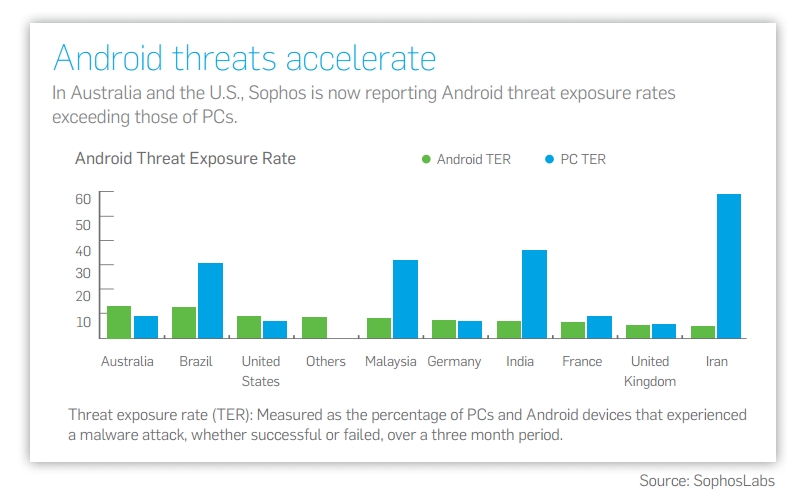
Compelling arguments can be made about the relative security of Google’s Android operating system versus Apple’s iOS, but the primary contributing factor to the spike in mobile attacks is that consumers don’t take the appropriate steps to secure and protect their devices, and CSPs don’t advocate for mobile security in a manner that’s consistent with threat levels. Even something as simple as setting a PIN number or passcode, although common in the PC world, isn’t widely employed by mobile users; in fact, a recent study commissioned by Sprint found that 44 percent of surveyed cell-phone users don’t secure their devices in this fashion.
Along with general mobile policies, CSPs should refine their focus on the security of BYOD implementations. IT departments in businesses large and small are turning to BYOD to lower equipment costs and simplify the digital lives of their workers, but it creates significant security challenges for the following reasons:
- workers’ personal devices operate outside of corporate firewalls;
- it’s difficult for a business to implement uniform security policies due to the proliferation of various device types and operating systems;
- more than 60 percent of devices used in BYOD environments lack data encryption.
Workers can access personal cloud storage and other cloud-related applications from the workplace, which should also be addressed, partly because those apps can be authenticated with a Facebook login. Businesses often have security policies in place to prevent use of unsanctioned external storage, but these policies haven’t yet caught up to the cloud revolution.
Machine-to-machine communications (M2M) are the third critical attack vector after the cloud and mobile, but only because M2M still isn’t widely deployed. As the number of unattended connected devices grows, however, we can expect to see an increasing number of M2M attacks, ranging from basic SIM-card fraud to more damaging attacks on core network services. Pipeline has previously reported on the security risks of M2M, and the bottom line is that most M2M devices are vulnerable to a variety of attacks.
Evolved threat prevention
As service provider organizations have grown, most have accumulated a vast amount of disparate hardware through acquisition, making unified security protocols difficult to actuate. The diversity of devices and platforms—supported devices as well as ones brought over to CSPs’ networks by customers—means virtually any connected device can become a surface from which to launch network attacks. Furthermore, coding isn’t just written in-house—it can originate from many different third-party sources, and it rapidly changes.



















