Funded Threats: The Fuel for Malware Evolution
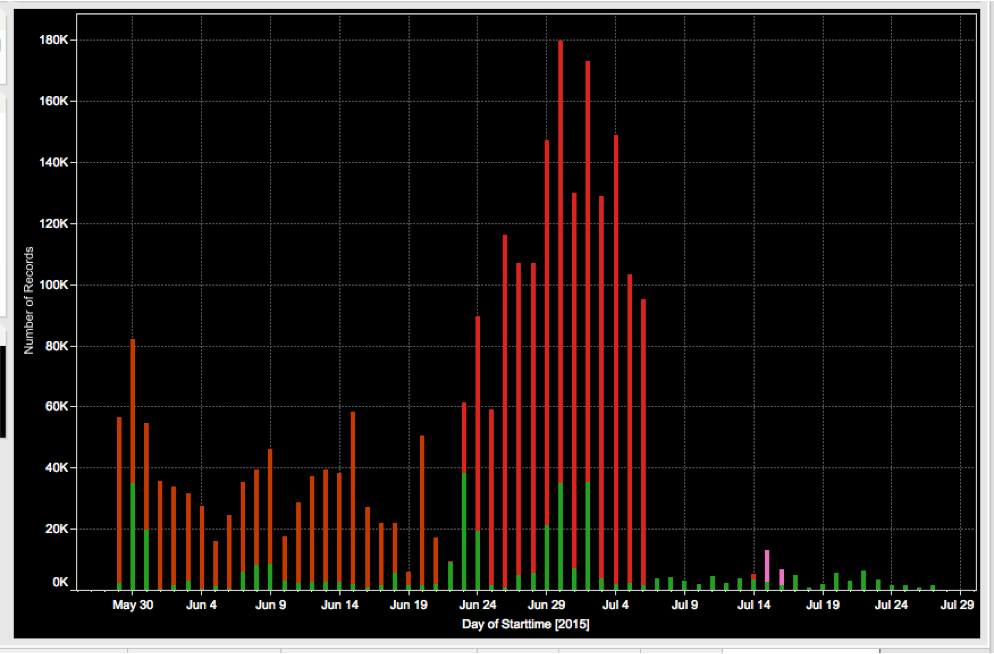
Normally a few machines with a DDoS client installed is not a very big concern; but, given the size of this brute force attack, there were likely tens of thousands of compromised machines now under the control of the threat actor.
This type of attack is very common, but it is rarely taken to these absurd lengths since it is so easy to spot. At this massive of a scale this DDoS network was a threat to large companies and even major portions of the Internet.
To combat this threat, our threat researchers, Level-3 and other communications service providers began blocking the actors' infrastructure on the Internet backbone. The threat actor attempted to migrate networks to avoid these blocks; but, due to the implementation of their network and the nature of the attack, they continued to be easy to spot. As of early July, the threat actor appears to have relented.
Conclusion
As the number of people and devices connected to the Internet increases, so does the financial gain for cyber criminals through their nefarious activity. This explosion in revenue, coupled with the adoption of bitcoin and anonymizing traffic protocols (Tor & I2P), have made for an evolving threat landscape.
Today, these threats are backed with large development efforts and are designed to compromise users delivering money to their creators quickly and effectively. While there are still more classic threats like SSH Psychos operating, this new group of threats designed for monetization is quickly growing and morphing, accounting for a larger portion of the threat landscape every day.
In the coming months, threats are destined to continue, evolve and expand; and it is up to communications service providers, as well as end users, to remain informed and vigilant in order to protect themselves – and their customers – from attacks on individuals as well as broader networks.



















