Securing a VPN Against Advanced Malware Threats
Assessing the threats
Companies that utilize VPNs so as to allow access to multiple partners and employees need to be concerned about hidden malware or APTs that might breach their perimeter defenses in the future or ones that may currently exist within the VPN core. These types of attacks can be instigated by a nation-state or by advanced hackers with a sophisticated set of tools and tactics designed to exploit the security infrastructure of the VPN.
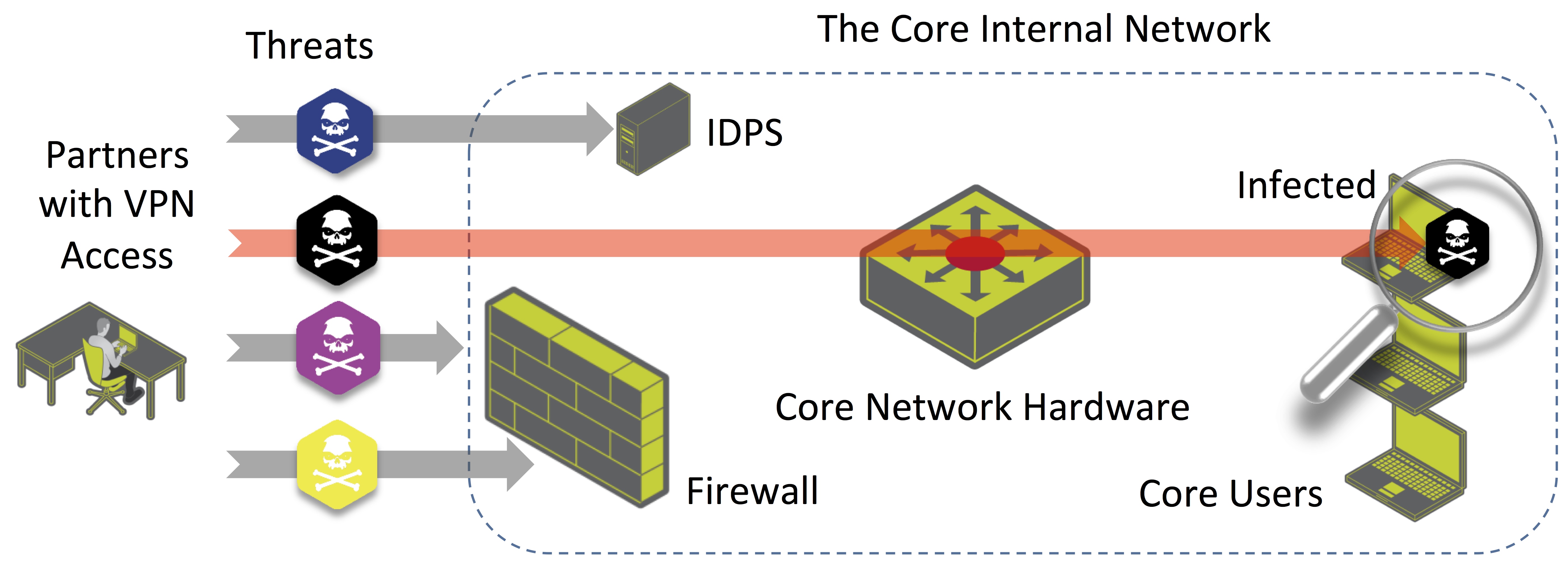
Take, for example, a company operating a large corporate network that serves multiple departments with Ethernet links of 10 Gbps (gigabits per second) leading into the core. The company also maintains a large data center on an isolated segment off of the core, while the perimeter is protected by a next-generation firewall and intrusion detection and prevention systems (IDPS). Threats, however, are still able to infiltrate the network and spread internally from host to host.
Due to the nature of the work that’s being conducted, the company’s IT department restricts partner and employee access to certain resources in the network through VPN tunnels. A primary goal of this department is to ensure that the restrictions put in place for the company’s partners aren’t circumvented, and that those partners only have access to the resources for which they’ve specifically been granted access. For this reason, the company requires a security system that can verify that the restrictions aren’t being bypassed and detect network activities that may result in a critical breach of data.
Another goal is to immediately identify suspicious behavior in the network and determine if certain systems have been compromised. If that’s the case, the next step is to identify which specific hosts are exhibiting this behavior.