What Can't Be Virtualized?
ASIC technology is also finding its way into the data center in a wide variety of applications. Very similar to FPGA technology, application specific integrated circuits perform data processing at extremely high rates; but, unlike FPGA or GPU technology, cannot be reprogrammed or have their algorithms updated in the field. Further, these types of devices tend to be very application specific and/or are designed to work with external devices, such as controls and sensors, not typically installed in the server chassis. Many of the components of the modern server include ASICs, such as USB and disk controllers and they are now finding their way into broader applications with the explosion of the Internet of things (IoT) and other non-traditional Internet-enabled computing devices.
Finally, with the increasing demand for more secure and trusted computing, hardware-based solutions for implementing cryptography, credential management and other aspects of cybercrime prevention are beginning to make serious inroads into the data center. These components, typically implemented as self-contained and separate devices such as HSMs, or integrated with existing server technology as trusted platform modules (TPM) will likely become ubiquitous in the coming decade. These components generally implementing the trusted platform module specifications defined as TPM 2.0, the latest specification for these types of devices (a good reference on this technology can be found in A Practical Guide to TPM 2.0 by Will Arthur and David Challener, published by Apress Open).
Characteristics
These components that don’t lend themselves easily to virtualization generally fall into one or more of several categories that result in problematic virtualization support.
This includes categories of components that are: (1) persistent in state with difficult or no means of preserving and restoring that state; (2) high-performance computing (HPC) components that perform poorly virtualized; (3) security components that rely on specific hardware to establish a root of trust; and (4) newer device technologies that simply do not yet have full virtualization support.
There are a wide variety of components that are making their way into the information technology landscape that exhibit one or more of these categories of problematic virtualization. The table below lists the most common problematic components and what issues they face.
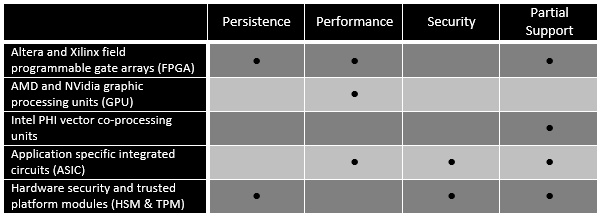
Persistence
The problem of persistent state creates an issue for virtualization in that it makes it very difficult for the component to be shared by multiple users and processes. As part of any good virtualization scheme, the virtualized component should behave as if it is being used by a single user or application. It should also be able to be rapidly provisioned and made available to multiple users or applications simultaneously. In systems that require or inherently have persistent state, virtualization becomes problematic, as persistence interferes with the ability to make the component appear as if it is operating for a single user or application.
In some cases, it is simply not possible to get the component to behave in such a manner that execution of one virtual instance doesn’t interfere with another. In many cases, access to these devices requires that they be dedicated to a single user or application and that additional code be written to manage this. They also tend to be deployed in a one-to-one relationship between the real hardware and a virtual instance, essentially limiting the virtualization to a single unit of the component to avoid the inherent persistence problem.



















