
article page
| 1 | 2 |
their own processing resources and therefore do not alleviate the monitoring equipment’s burden of too much data, nor do they provide traffic aggregation functionality. Additionally, they drain optical power from the network.
A smarter solution comes in the form of optimizing traffic prior to monitoring equipment. Here, the term “optimization” is an umbrella term for link aggregation, packet/service filtering, interface/protocol translations, and other tactics intended to streamline the data for specific monitoring needs. These devices can be used to front-end multiple tools that are monitoring different services, sending only the data of interest to each tool. Consequently, tools are able to become more efficient and require less up-front processing resources, allowing them to focus on what they do best, such as measuring the Quality of Service of VoIP traffic. Another added benefit of this monitoring access solution is that the life of a monitoring tool is lengthened since these products can also perform filtering and interface translations as data speeds increase and protocols change. Figure 1 below shows a data access configuration where one of these devices accesses converged network traffic and directs it to specific tools for higher-level processing.
|
|
A smarter solution comes in the form of optimizing traffic prior to monitoring equipment. |
|

wasted due to its stateless nature. Resources are wasted because an application on the near end of a transmission will continue to use network resources even when the application on the far end is no longer available.
Today, network administrators solve this tunneling problem by positioning monitoring tools behind the access router so that the tunnels are already stripped off of the payload. While this solution does eliminate the issues related to tunnels, it introduces several new complications. First and foremost, it raises doubts as to whether the data was compromised before or after the router. It also masks issues relative to WAN network performance. In order to monitor all network traffic, tools and probes need to be equipped to identify and process all data, whether it is traversing the network as IP or GRE.
While several flavors of solutions are available in the market today that address one or the other of the problems discussed above, only a few combine the valuable functionalities of optimized access and tunnel identification/processing.
|
|
|
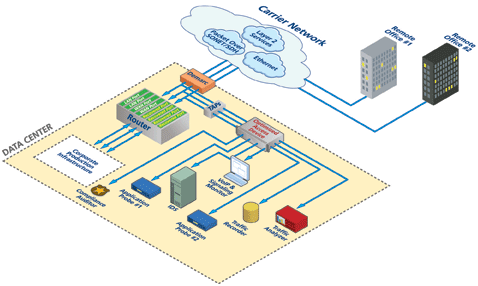
Figure 1
(Click image for larger view.)
|
|

The increase in tunneled protocols within converged networks complicates monitoring strategies even further. The Generic Routing Encapsulation (GRE) protocol, for example, is a widely used tunneling protocol that creates a virtual point-to-point link between routers and remote points in an IP network through IP tunnels. GRE has created a void in network monitoring strategies because many probes or tools cannot remove its tunnel header. The result is that GRE data is often not monitored, which is problematic because network administrators need a comprehensive view of the network in order to effectively anticipate and troubleshoot problems. Furthermore, monitoring the GRE protocol is even more necessary since network resources are easily
|
|

Network administrators looking for a fool-proof monitoring strategy need to consider not only the new and improved monitoring tools available today, but also monitoring access optimizers that empower these tools to be more comprehensive and cost-effective.
|
|




