article page
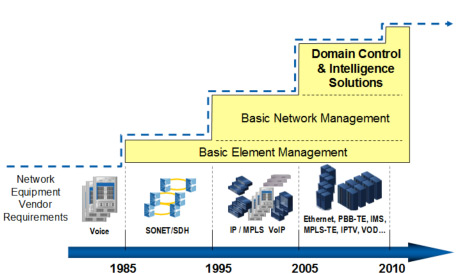
| 1 | 2 | 3 | than single vendor Element Management solutions and even more than stovepipe Network Management solutions.
DCI applications treat your network devices as a network, not groups of individual nodes.
DCI applications offer the ability to automate the manual steps found in these MOPs through predefined application workflows or by configurable workflows. By automating the MOPs, the average operator can now successfully and accurately perform these steps.
Studies have shown that 70% of outages are caused by manual operations, making the automation and control of manual network touches a key element to improving network management efficiency. These elements are a key foundation of DCI applications.
|
|
Studies have shown that 70% of outages are caused by manual operations. |
|

Regional, or local parameters. This solution offers a very efficient way to compare deployments without individual login to subcomponents. Errors caused by manual actions are quickly identified as deviances and can be quickly reset to “approved” parameter values.
An associated DCI solution is a workflow capability that automates the manual steps involved in the initial configuration or commissioning of IMS, VoIP, or IPTV deployments. Complex manual parameter settings can now be highly automated, streamlining the commissioning process so that, beyond initial IP address configuration,
|
|
|
|

One DCI solution can offer a Single Sign-On (SSO) proxy across these deployments, ensuring that operations staff use their own login credentials, and are offered access only to those subcomponents that their job function should allow them to access, completely eliminating shared credentials. This type of proxy allows operations staff controlled access to subcomponents through appropriate interfaces through a single portal, while ensuring that the right type of access is permitted based on the privileges for that user. A single point of security administration is offered, allowing administrators to manage user and group credentials and privileges, ensuring that operations personnel access is “right-sized.” Furthermore, security administrators have access to full centralized logs of user sessions should outages need to be investigated and forensically traced for root cause analysis.
Another DCI solution offers the ability to compare configuration data for specific subcomponents at very fine granularity with either similar subcomponents or templates that break down parameters into National,
|
|

very few manual steps need to be initiated by the installer. No longer is the rapid deployment of new equipment dependent on each installer accurately configuring complex manual parameter settings immediately after power up. Accurate commissioning of newly deployed devices is now centralized, controlled, and tracked.
Backup and Restore is a key DCI solution that centrally backs up each subcomponent in a uniform manner, ensuring that the latest configuration data for each subcomponent is available should catastrophic failures occur, resulting in the loss of volatile store. There is a lot of comfort in knowing that the configuration data for each and every subcomponent of your IMS, IPTV, or VoIP solution is being properly backed up to ensure that recovery is straightforward.
The Network Audit and Software Delivery DCI application automates the upgrade process by first performing a series of software, alarm, and hardware audits, ensuring that the typical
article page
| 1 | 2 | 3 | |
|