|
|

article
page | 1 | 2 |
3 | 4 |
such as IMS,
increasing demands will be made
on systems that collect and correlate
such data.
In the U.S.,
roving surveillance requirements
are specified in Section 206
of the U.S. Patriot Act. This
measure has had profound impact
on lawful interception methods,
since it expands the scope of
surveillance beyond a single
communications identity to multiple
communications identities associated
with a target. For example, multiple
fixed line and mobile phone numbers,
e-mail addresses, SIP addresses,
and other identifiers may now
be involved in correlating
the traffic of various service usage
for a particular person or persons
of interest.
Finally, in
a controversial ruling, the Federal
Communications Commission (FCC)
has required that operators of
broadband Internet and interconnected
Voice-over Internet Protocol
(VoIP) services establish systems
to enable law enforcement agencies
to process wiretapping requests.
While standards are not finalized
for this technology, it is clear
that these services are next
to be brought under surveillance
and control.
Other
legislative concerns
In the meantime, the
Wireless Communications and
Public Safety Act of 1999
required as a feature of the 911
emergency-calling system that operators automatically
associate a physical address with
each calling party’s telephone
number. This data enrichment was
unneeded for broadband
and VoIP services until recently, when
in 2005 the FCC required that VoIP
services that interconnect with
the public telephone network begin
to provide 911 service, as well
as provide notice to their consumers
concerning the 911 limitations.
As mandated,
the E911 hookup may be directly
|
|
Ultimately, implementing a lawful
intercept and surveillance solution
and strategy is no longer a choice;
it’s a necessity.
|
|

with the wireline E911 Network,
indirectly through a third party
such as a competitive local exchange
carrier (CLEC), or by any other
technical means, although some
VoIP providers remain significantly
out of compliance with the order.
The
Sarbanes-Oxley Act was established
in 2002, requiring that all operators’ internal
systems and operational controls,
pertaining to business activities
and financial reporting, produce
audit evidence that can be tracked,
monitored, and ensured by the
management team of the companies.
In short, above
and beyond the operators’ own
requirements to collect, mediate,
store, and distribute call records
for service usage, there is increasing
pressure to handle processing
of this service usage for other
reasons, often in real-time,
and sometimes involving very
processing-intensive correlation
and business rules.
How
is all of this done?
The lawful interception
standards proposed by ETSI have
provided the dominant reference
model that is currently applied
in Western countries worldwide.
Although there are slight variations
in terminology according to region
and to address specific verticals
(e.g., Cable/MSO), the ETSI model
is essentially the same as the
predominant architecture deployed
throughout the U.S. to achieve
CALEA compliance.
See Figure
1 – Lawful Intercept
Reference Model representing
a composite view based on ETSI
and TIA standards and terminology. |
|
|
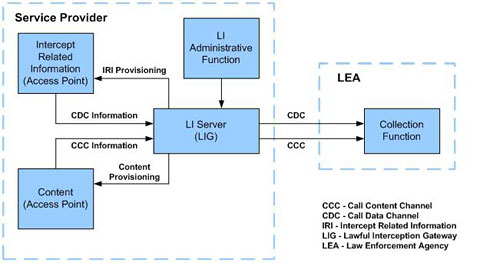 Figure
1 – Lawful Intercept Reference
Model
Figure
1 – Lawful Intercept Reference
Model |
|
 |

article
page | 1 | 2 |
3 | 4 | |
|
|




